Queer pub forced to abort HIV fundraiser amid sickening ‘Operation Pridefall’ anti-LGBT+ cyber attack

The Eagle, an LGBT+ bar in London, England. (eaglelondon/twitter)
A British LGBT+ bar had its online HIV fundraiser ground to a juddering halt after homophobic 4chan users staged an Operation Pridefall cyber attack.
The Eagle, a pub in south London, England, hosted an online stream of its regular Sunday night party, Horse Meat Disco, on May 31 to raise money for HIV charities in the capital.
Less than two hours in, organisers posted to the event’s Facebook page that they were having “technical difficulties with the MixCloud stream” as the event fell victim to the ongoing Operation Pridefall cyberattack.
A little more than 10 minutes later, they announced the event was going offline and would be rescheduled to next week.
“We’ve done everything we can but sadly defeated by tech,” they wrote.
The Eagle’s owner, Mark Oakley, told the Independent how its Facebook Livestream was clogged with 110 spam bot accounts, leading to the event going offline,.
The comment sections under both Facebook posts were crammed with what appear to be fake or hacked accounts posting sham links to the streamable event.
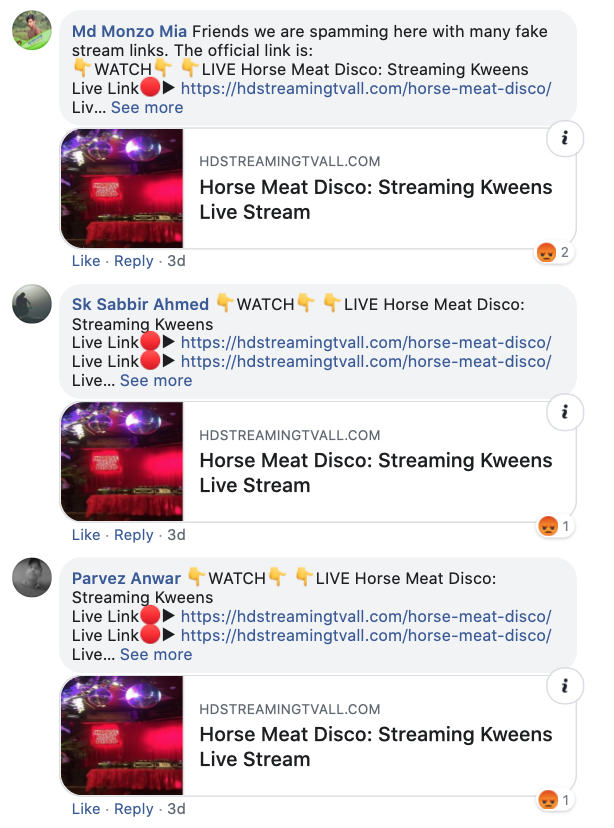
The comment sections under the HIV fundraisers were snarled by purportedly scam accounts sharing fake links. (Facebook)
Oakley added that the Mixcloud stream set up to allow thousands join from home was shut down, too.
“Having done several dry runs with everything working perfectly well we ran into immediate difficulties when everyone tried to join,” he explained.
Operation Pridefall plots to spam LGBT+ community.
The Eagle’s shutdown comes after Metropolitan Police, the force responsible for law enforcement in London, explained that officers are “aware of and prepared” for the digital attacks.
Members of the imageboard website 4chan have organised “Operation Pridefall”, which according to archived threads is a two-pronged attack against the community
Members plan to create a swarm of artificial accounts to spam LGBT+ users.
Moreover, they aim to boycott companies that show support during Pride Month and stuff poisonous homophobic propaganda in the brand’s social media accounts.

Users of an alt-right 4chan board are conspiring a cyberattack against the LGBT+ community. (4chan)
Pockets of LGBT+ people have begun reporting receiving direct message requests from unknown users. Accepting them tends to lead to inboxes being stuffed with hateful messages and, at times, graphic videos, victims report.
“Radicalising people works a lot better when people don’t associate you with hate and extremism,” an undercover source embedded in the group’s chat rooms told PinkNews, “so they create these accounts and masquerade as LGBT-critical liberals”.
However, the source stressed that while a few “lone wolves” are doxxing some queer users, “[doxxing] isn’t part of their operation.”
Overall, they said, “the group doesn’t have much of an interest in targeted individuals”.
“Everyone can do their part in reporting and blocking suspicious pages that are sharing homophobic content,” they continued.
“Things to look out for are new and empty accounts, especially those created in May and June. They’re also using AI-generated faces as profile pictures, so here’s a good guide on how to spot these.”

